This is my writeup for the UCTF’s Secret Password Stash.
Challenge Description
I’ve created the best system for storing all my top-secret information. Hackers can’t steal my secrets if I store them in a virtual machine, right? Unfortunately, I accidentally deleted the virtual machine. Oops! Luckily, I saved a memory capture. Can you help me recover my lost passwords? The flag will be in format - uCTF{flag}
Summary
In this challenge, a memory dump was analyzed to recover a lost password. By using the Volatility Framework, the password database of the software pwsafe.exe was identified and dumped. Two methods were then used to discover the master password: checking a .txt file, and extracting it from the user’s clipboard. Using this master password, the database was decrypted with Password Safe to retrieve the flag
Note that all commands are for Volatility 3, unless otherwise noted.
Discover the Password Database
Let’s start by finding the Windows version:
python3 vol.py -f memory.dmp windows.info
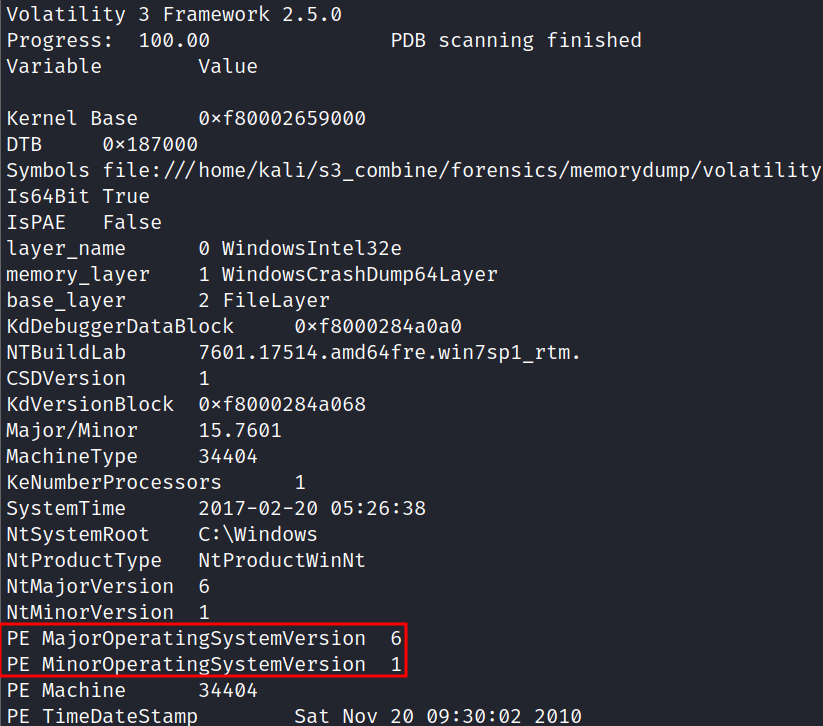 This memory dump uses Windows 6.1(Windows 7).
This memory dump uses Windows 6.1(Windows 7).
Let’s list the processes:
python3 vol.py -f memory.dmp windows.pslist
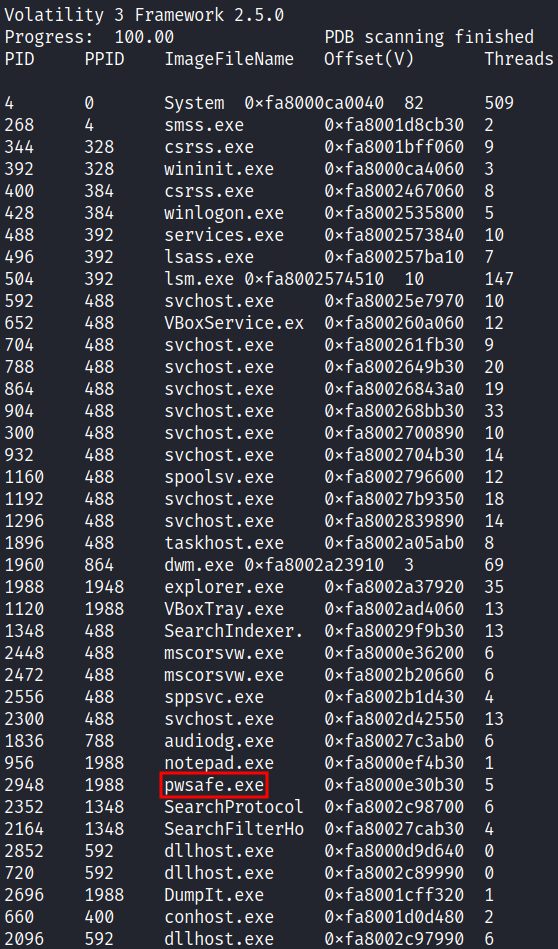 The first binary that stands out is
The first binary that stands out is pwsafe.exe. This is likely the software that is storing the flag. After some research, I deducted this application uses the .psafe3 file extension to store the password database.
Search for any files with the psafe3 file extension:
python3 vol.py -f memory.dmp -o ../ windows.filescan | grep psafe3
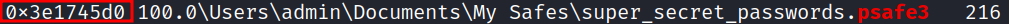
We found the password database. Let’s dump it to our system, using the memory address we found in the previous step:
mkdir dump_files
python3 vol.py -f memory.dmp -o dump_files windows.dumpfiles --physaddr 0x3e1745d0
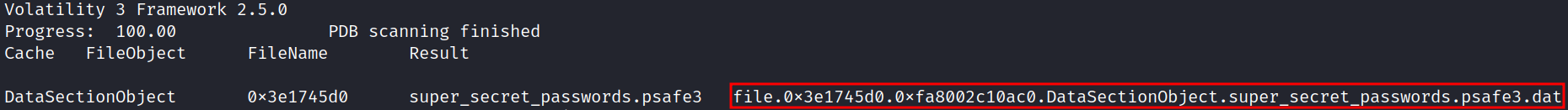 We get the database dumped to our system. However, we need the master password to decrypt it.
We get the database dumped to our system. However, we need the master password to decrypt it.
Discover the Master Password
The master password can be discovered in several ways.
- Find the
.txtfile that stores the master password in plain text:
python3 vol.py -f memory.dmp windows.filescan | grep txt
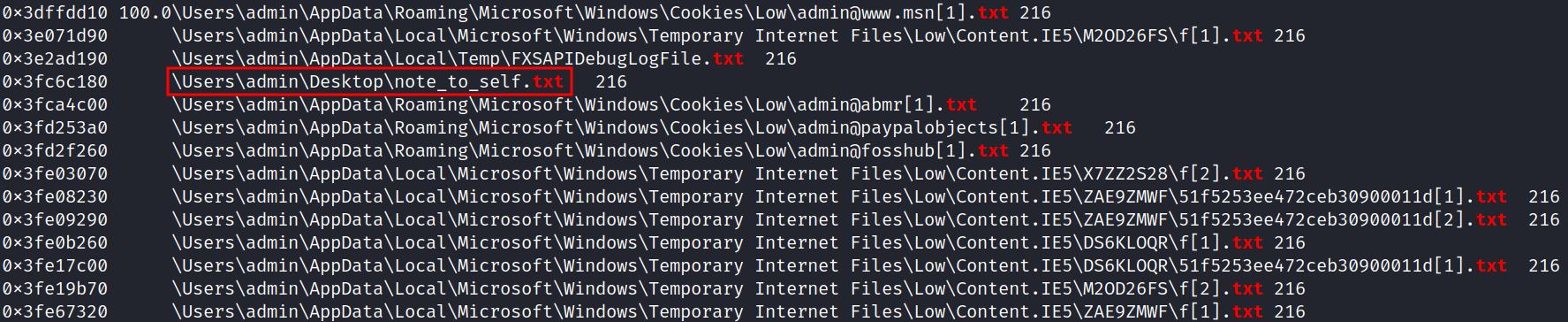
Dump note_to_self.txt to disk using the previously displayed memory address:
python3 vol.py -f memory.dmp -o dump_files windows.dumpfiles --physaddr 0x3fc6c180
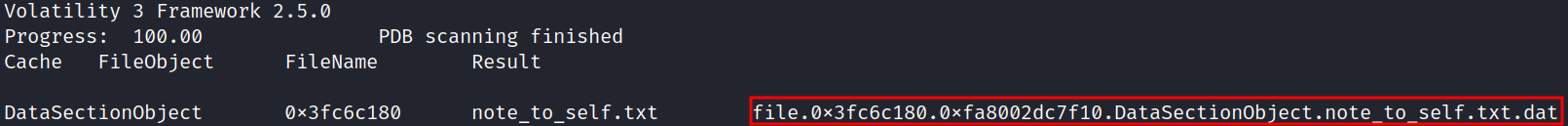 This file contains the master password.
This file contains the master password.
- Extract it from the user’s clipboard (volatility2):
# The profile was determined from the previous output of windows.info
python vol.py -f memory.dmp --profile=Win7SP1x64 clipboard
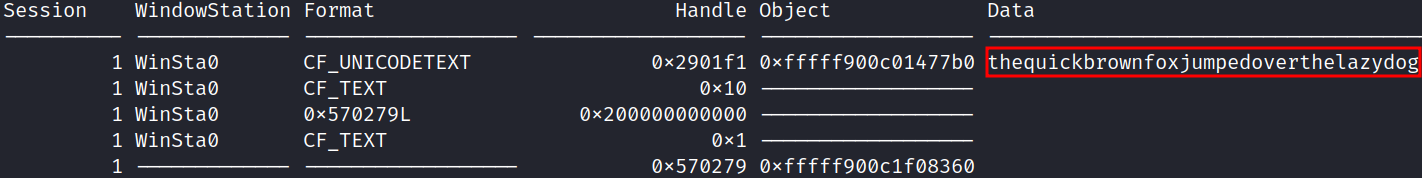 Master Password:
Master Password: thequickbrownfoxjumpedoverthelazydog
Decrypt the Database
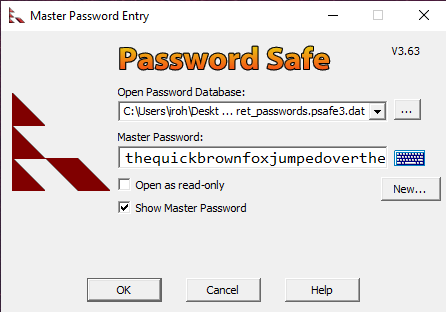
Download Password Safe, and run it.
Select the password database, enter the master password, and hit OK:
Double click flag [] to copy the flag to your clipboard:
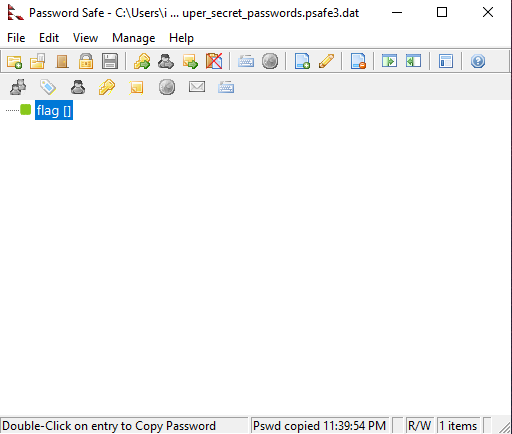
Flag: uCTF{Suppa_secret_pa$$word}